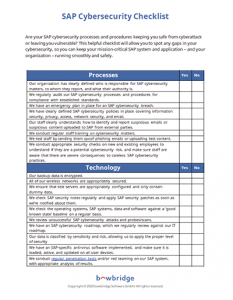
1. How long do most companies take to detect a data breach, even a major one?
Best Answer: d.
6 months
Equifax, Capital One and Facebook are just a few of the companies who were hacked in recent years and didn’t discover the intrusion for at least six months. According to the Ponemon 2017 Cost of a Data Breach Study, US companies take an average of 206 days to detect a data breach.